Technologies
With the rise of cloud computing and adoption of a Software as a Service (SaaS) approach, the way software is delivered has changed. Cloud computing and SaaS not only enable software to be used over the internet, but they also reduce costs and energy consumption by sharing resources among multiple customers. However, the privacy of customer data must be still protected. Ensuring customer privacy is a key aspect of building a successful SaaS solution. Helbling has successfully demonstrated that data privacy implemented by design ensures regulatory compliance in an economically scalable way and results in trust and confidence from customers.
As sustainability has become a priority, the new sustainability paradigm should include software solutions that support achieving economic growth while operating with a minimal ecological footprint. Leveraging cloud-native technology and modern software architecture can bring efficiency to the next level for globally scaled Software-as-a-Service solutions. However, global compliance is a great challenge and must be addressed from the beginning. By following data privacy and data ethics programs, companies can not only sustain regulatory compliance, but also achieve positive social outcomes. Helbling has recently implemented projects in different industries in which these aspects have been addressed.
Sustainability in the cloud becomes a priority
Sharing resources among multiple SaaS customers in cloud computing is tempting, because it not only reduces costs but also reduces the overall energy consumption and carbon footprint of a software application. Built on top of cloud data centers, efficiency is improved on multiple levels:
First, public cloud providers continuously improve the energy efficiency of their data centers [1]. Reliable measurements are established to consistently follow the path to net zero. Microsoft, for example, announced the power usage effectiveness (PUE) and water usage effectiveness (WUE) metrics to measure energy and water consumption in their data centers [2].
On the next level the same physical hardware (such as computing power, networking, and storage) can be shared by multiple applications thanks to virtualization.
Finally, if a dedicated instance of an application service is deployed per customer (as was done traditionally with desktop applications) this simply does not scale economically. This last level is new for companies that have not previously operated software solutions in the cloud.
Fitting software for hearing aids needs to be reliable and easy to use
In a recent project, Helbling led the SaaS adoption of a global manufacturer of hearing aids. The solution provides a fitting service that enables hearing care professionals to meet their individual patients’ needs by optimally configuring the hearing aids. Traditionally, the hearing care professionals used a desktop software application for fitting. The software was replaced by a new SaaS offering running in the cloud, requiring only a web browser to access and use the fitting application.
While big chains are important customers using SaaS, there are also many health care professionals that work for small organizations and only occasionally use the provided application services but still expect the same quality of service. This is a perfect example where multitenancy is required to scale economically.
Multitenancy brings new challenges and data privacy concerns
SaaS must take it to the next level and apply resource sharing not only to hardware but also to the application services built on top of virtualized hardware, which are then used to serve multiple customers. The provider of the SaaS solution manages the software and infrastructure needed to deliver the application service to the end customers of the application. Therefore, reducing maintenance effort is essential. These end customers are often referred to as tenants. To support serving multiple tenants, a multitenancy architecture is required.
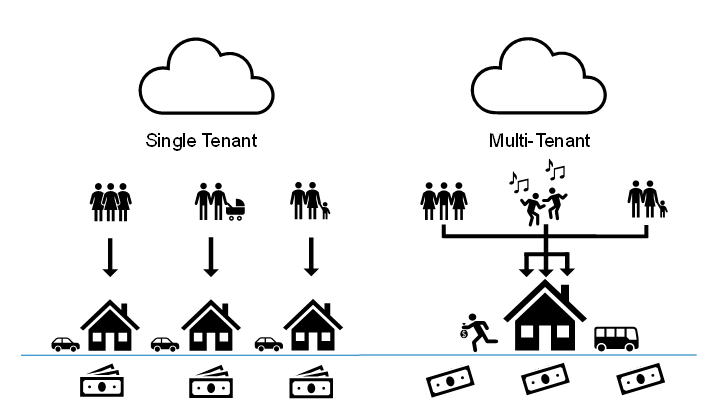
Such architecture must ensure that, while tenants share resources, they are not aware of each other, and their data is kept separate. The first issue is known as the "noisy neighbor effect", which happens when one application uses most of the available resources and has an effect on others, such as creating performance problems. The second relates to data protection. This is especially important for healthcare organizations as they are being increasingly targeted by cybercriminals due to the vast amounts of patient data they process.
Data residency and sovereignty as key aspects
Several data breaches that have become public have increased concerns that private data is being sold or shared with third parties without users' consent. This global concern has translated into several laws, regulations, standards, and guidelines that seek to protect user data and privacy (see fact box). According to UNCTAD [4], 137 out of 194 countries have introduced legislation. Although some of the laws are the same in certain regions, global compliance is a great challenge.
As a company's data footprint grows, so does the threat landscape and with it the regulations requiring compliance. Companies handling international data must ensure that data protection is not compromised when data is shared across borders. Regulations depend not only on where data is collected but also on where it is physically stored.
There are two important definitions that are worth clarifying here: The term data residency refers to where the data is physically and geographically stored, while the term data sovereignty includes not only where the data is stored but also the laws and regulations that apply to the storage and processing of data in its physical location (see fact box).
How Helbling has overcome these challenges
A data breach occurs when information is obtained by an unauthorized party in a fashion in which it was not intended to be made available. By applying encryption (at rest and in transit), only authorized parties can access sensitive information. However, encryption at rest and in transit (even if applied end to end) is not enough in SaaS with multitenancy architecture. As the application instance handles requests from multiple companies, the conclusion that an application code would have access to all companies’ data would neither follow the principle of least privilege nor the mindset of zero trust [3].
Moreover, if data access is granted on application level, bugs could lead to an unintended data breach.
While developing the fitting SaaS, Helbling instead introduced data privacy protection at the infrastructure level. A gatekeeper was introduced that removes the burden from application services to need to know how to store and transfer data in compliance with data privacy regulations. The gatekeeper locates the data in the underlying database topology and validates requests against regulations.
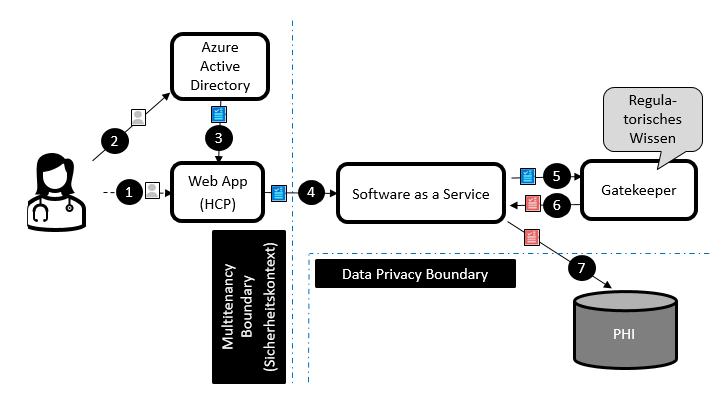
As shown in Figure 2, a request for patient data starts when the health care professional user (HCP) signs into the application (1). Authentication takes place at the identity provider (2), where the HCP’s credentials will be checked. The access token returned (3) provides the security context (tenant) for the signed-in user. A valid access token (cryptographically signed by the trusted identity provider) is needed to cross the multitenancy boundary (4).
The access token cannot be used directly to access data. Instead, the application must exchange the access token (5) for a short-lived token (6) that is limited in scope. The gatekeeper applies fine-grained permission control following the least privilege principle. With this token, the data privacy boundary can be passed (7) to finally access the data needed to answer the request from the HCP.
If transmission of data is not allowed due to regulations (e.g., HCP tries to access data from a foreign country), the gatekeeper will deny access.
Summary: Sustainable SaaS solutions respecting data privacy are feasible if data privacy aspects are considered from the beginning
When developing Software-as-a-Service solutions on a global scale in which both sustainability and the protection of personal health data must be addressed, an appropriate architecture is crucial. Helbling is an experienced partner that has successfully developed global SaaS solutions in the past. Data protection and regulatory requirements have been considered early in development and addressed by design, allowing the business to scale economically in accordance with demands.
Authors: Frederic de Simoni, Laura Santos Carreras
Main Image: AdobeStock
[1] Microsoft, 2020: The carbon benefits of cloud computing: A study on the Microsoft Cloud in partnership with WSP, https://www.microsoft.com/en-us/download/details.aspx?id=56950
[2] Walsh, N., 2022: How Microsoft measures datacenter water and energy use to improve Azure Cloud sustainability, https://azure.microsoft.com/en-us/blog/how-microsoft-measures-datacenter-water-and-energy-use-to-improve-azure-cloud-sustainability/
[3] Rühl, T., De Simoni, F., Anliker, U., 2023: How cyber security is integrated in the development of connected products, https://www.helbling.ch/how-cyber-security-is-integrated-in-the-development-of-connected-products/?lang=en
[4] United Nations Conference on Trade and Development - Data Protection and Privacy Legislation Worldwide, https://unctad.org/page/data-protection-and-privacy-legislation-worldwide
[5] IBM - Cost of a data breach 2022 A million-dollar race to detect and respond, https://www.ibm.com/reports/data-breach





